Pharma hack repercussions
-
I just recently cleaned up a pharma hack for someone and they are still seeing emails being sent out with his domain as a link for the link target.
Anyway to fix that? does that stop after a while? do all the links that are out there with his domain in it affect his SEO in a way that he could be misconstrued as doing black hat SEO techniques?
thanks
-
if you have a pharma hack should use Sucuri even if you have had your site cleaned up by Google Webmaster tools I would run it through the free site check at the link below. Then look at all the advantages to just $89 the year plus if you get hacked ever again during that year who is fixed 100% free. They're fast very good and will have your site running normally again.
run your website through this free scanner and read below
http://sitecheck.sucuri.net/scanner/
rather or not you are running a CMS like WordPress does not make much of a difference however in this tutorial or discussion regarding tarmac is focused on WordPress however all of these things would be happening to any website.
http://blog.sucuri.net/2010/07/understanding-and-cleaning-the-pharma-hack-on-wordpress.html
&
http://blog.sucuri.net/tag/pharma
I even have a live one right here for you I would not give you the actual URL but this is the cleanup URL
http://sitecheck.sucuri.net/results/worldluxurynetwork.com
Understanding and cleaning the Pharma hack on WordPress
july 13, 2010 by david dede 52 comments
In the last few weeks, the most common questions we’re receiving are related to the “Pharma” (or Blackhat SEO Spam) Hack on WordPress sites.
This attack is very interesting because it is not visible to the normal user and the spam (generally about Viagra, Nexium, Cialis, etc) only shows up if the user agent is from Google’s crawler (googlebot). Also, the infection is a bit tricky to remove and if not done properly will keep reappearing.
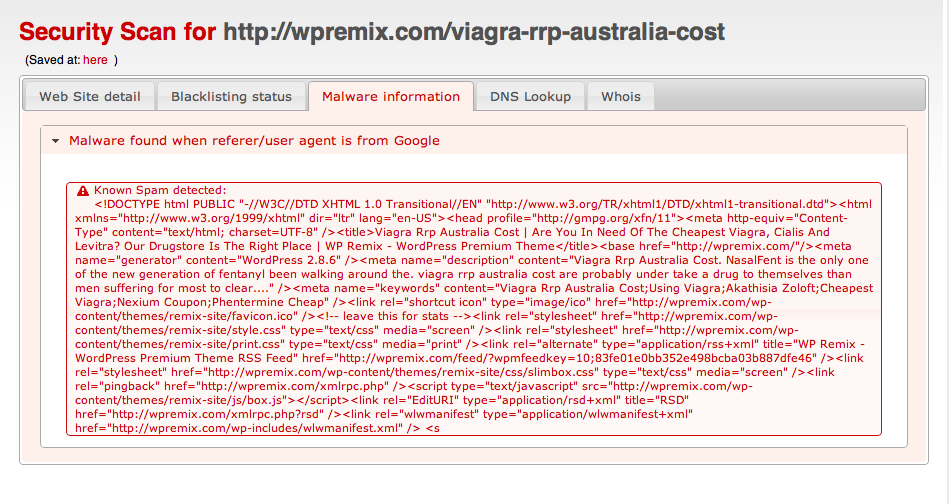
Because of this behavior, many sites have been compromised for months with those spam keywords and no one is noticing. A quick way to check if your site is compromised is by searching on Google for**“inurl:yoursite.com cheap viagra or cheap cialis”** or using our security scanner.
For example, this is the result of our scanner against wpremix.com (which was infected at the time we were writing this post):
Pharma Hack – details
The Pharma Hack has various moving parts:
1 – Backdoor that allows the attackers to insert files and modify the database.
2 – Backdoor inside one (or more) plugins to insert the spam.
3 – Backdoor inside the database used by the plugins.If you fix one of the three, but forget about the rest, you’ll most likely be reinfected and the spam will continue to be indexed.
As always, we recommend that you update your WordPress instance to the latest version. This goes for all of your plugins, themes, etc. WordPress is typically very secure, it’s when you’re running old versions, and/or out of date plugins/themes that run into trouble. Keep your stuff up to date, and it will minimize the risk of infection significantly.
1 – Backdoor that gives remote access to the users
This is the first step in the infection. Generally attackers do large scale scans and try to inject the backdoors into compromised sites. They do this by searching for vulnerable WordPress installations (older versions), vulnerable plugins, hosting companies with known security weaknesses, etc.
When the backdoor is added, it is not immediately executed. Sometimes it stays for months without ever getting called. The common places for these backdoors are:
wp-content/uploads/.*php (random PHP name file)
wp-includes/images/smilies/icon_smile_old.php.xl
wp-includes/wp-db-class.php
wp-includes/images/wp-img.phpCharacteristically in the past, these files have had an “eval(base64_decode”, ultimately that’s what most people recommend searching for. However, on the pharma attack, the backdoor starts with:
< ? php $XZKsyG=’as’;$RqoaUO=’e';$ygDOEJ=$XZKsyG.’s’.$RqoaUO.’r’.’t';$joEDdb
=’b’.$XZKsyG.$RqoaUO.(64).’_’.’d’.$RqoaUO.’c’.’o’.’d’.$RqoaUO;@$ygDOEJ(@$j
oEDdb(‘ZXZhbChiYXNlNjRfZGVjb2RlKCJhV1lvYVhOelpY… (long long string)..So, it still calls “eval(base64_decode”, but using variables making it harder to detect. In fact, none of the WordPress security plugins are able to find it. Our suggestion is to search for “php $[a-zA-Z]*=’as’;” also. After decoded, this is the content of the backdoor: http://sucuri.net/?page=tools&title=blacklist&detail=3ec33c4ab82d2db3e26871d5a11fb759
If you do an inspection of the code, you will see that it scans for wp-config.php, gets the database information, acts as a remote shell and retrieves a lot of information about the system.
That’s the first thing you have to remove before you do anything else.
2 – Backdoor inside one of the plugins
This is the second part of the attack. After successfully creating a backdoor into the system, a file will be created inside one of the existing plugins. Example:
akismet/wp-akismet.php
akismet/db-akismet.php
wp-pagenavi/db-pagenavi.php
wp-pagenavi/class-pagenavi.php
podpress/ext-podpress.php
tweetmeme/ext-tweetmeme.php
excerpt-editor/db-editor.php
akismet/.akismet.cache.php
akismet/.akismet.bak.php
tweetmeme/.tweetmem.old.phpNote that they will infect one or more of your enabled plugins and use names like wp-[plugin].php, db-[plugin].php, ext-[plugin].php, or something similar. We do not recommend you rely only those samples for your search, but try looking for any plugin file with the “wp_class_support” string on it.
$ grep -r “wp_class_support” ./wp-content/plugins
If you are infected, you will see things like (full content of the file here

./wp-content/plugins/akismet/db-akismet.php:if(!defined(‘wp_class_support’)) {
./wp-content/plugins/akismet/db-akismet.php: define(‘wp_class_support’,true);Make sure to remove those files. To be 100% sure your plugins are clean, I would recommend removing all of them and adding from scratch (not possible for all sites, but this is probably the most secure way of doing it).
3 – Backdoor inside the database
This is the last step, and equally important. This is where the spam itself is hidden. They have been using the wp_options table with these names in the “option_name”:
wp-options -> class_generic_support
wp-options -> widget_generic_support
wp-options -> wp_check_hash
wp-options -> rss_7988287cd8f4f531c6b94fbdbc4e1caf
wp-options -> rss_d77ee8bfba87fa91cd91469a5ba5abea
wp-options -> rss_552afe0001e673901a9f2caebdd3141dSome people have been seeing “fwp” and “ftp_credentials” being used as well, so check there too.
These SQL queries should clean your database:
delete from wp_options where option_name = ‘class_generic_support’;
delete from wp_options where option_name = ‘widget_generic_support’;
delete from wp_options where option_name = ‘fwp’;
delete from wp_options where option_name = ‘wp_check_hash’;
delete from wp_options where option_name = ‘ftp_credentials’;
delete from wp_options where option_name = ‘rss_7988287cd8f4f531c6b94fbdbc4e1caf’;
delete from wp_options where option_name = ‘rss_d77ee8bfba87fa91cd91469a5ba5abea’;
delete from wp_options where option_name = ‘rss_552afe0001e673901a9f2caebdd3141d’;Conclusion
Tricky stuff! The attackers are getting better and we have to learn how to protect our sites and our servers. If you need any help cleaning up the mess or you need a partner to help with your security needs, Sucuri is here to assist.
Protect your interwebs!
Malware Removal
We love destroying malware, and we’ve been at it for a while!
Our removal process uses our proprietary engine. It has been collecting malware definitions since 2004. Its history can be traced to early open source projects we released before becoming close source in 2008, and later formed into a company, Sucuri, in 2010. You can find information on the early incarnation of the engine by looking at Owl, version .1, and the Web Information Gathering System (WIGS).
What does the Cleanup Process Consist Of?
The cleanup process has been refined over the past few years. It’s very effective, but continues to evolve. The process is both manual and automated. The automated elements are quite restricted. Every cleanup is handled by a malware analyst whose responsibility it is to look through the results, identify anomalies and clean manually as required. The beauty of it is that the cleanup is included in every package for the no additional fees.
Yes – cleanup is included in every plan!
What do you Clean?
As malware evolves, so will our service. Under the current cleanups we include remediation for the following:
- Obfuscated JavaScipt Injections
- Hidden & Malicious iFrames
- Embedded Trojans
- Phishing Attempts
- Cross Site Scripting (XSS)
- Malicious Redirects
- Backdoors (e.g., C99, R57, Webshells)
- Stupid, Pointless, Annoying Messages (SPAM)
- Defacement
- Anomalies
- SQL Injection
- IP Cloaking
- Social Engineering Attempts
- Drive-by-Downloads
How do you Clean?
In most instances our cleanups are conducted remotely, using preferably SFTP, but also HTTP and FTP. Because of the challenges with HTTP, specifically time-outs and other connection issues, we may request secure shell (SSH) access.
Once we have access to your server we load tools that allow us to authenticate with the mothership. This connection allows us to traverse your server files and databases.
How am I Notified?
The internal ticket system uses the same notification options set in the alerting section. When a ticket is updated you are notified via email, you must log in to the system and update the ticket.
It’s Not Automated?
Unfortunately, no, not at this time.
Here’s why:
- We require access to your server in order to perform the remediation process.
- We do not offer services as a ‘Password Manager’ so we do not create or reset existing passwords.
- After every cleanup the first change we ask you to make is to update every password you have (i.,e., administrator page, database, FTP, SFTP, SSH, etc.. )
- We prefer to have a trained malware analyst working with each client.
Sincerely,
Thomas
Got a burning SEO question?
Subscribe to Moz Pro to gain full access to Q&A, answer questions, and ask your own.
Browse Questions
Explore more categories
-
Moz Tools
Chat with the community about the Moz tools.
-
SEO Tactics
Discuss the SEO process with fellow marketers
-
Community
Discuss industry events, jobs, and news!
-
Digital Marketing
Chat about tactics outside of SEO
-
Research & Trends
Dive into research and trends in the search industry.
-
Support
Connect on product support and feature requests.
Related Questions
-
Site Hack In Meta Description
Hey MOZ Community, I am looking for some help in identifying where the following meta description is coming from on this home page - https://www.apins.com. I have scrubbed through the page source without being able to locate where the content is being pulled from. The website is built on WordPress and metas were updated using Yoast, but I am wondering if an installed plugin could be the culprit. On top of this, I have had a developer take a look for the "hack" and they have assured that the issue has been removed. I have submitted the URL in GSC a couple of times to be re-indexed but have not had much luck. Any thoughts would be much appreciated, the displayed description is below. The health screening plays http://buyviagraonlineccm.com/ a significant and key role in detecting potentially life-threatening illnesses such as cancer, heart ...
Technical SEO | | jordankremer0 -
Manual action due to hack
We have had some issues with one of our websites getting hacked. The first time it happened, we noticed it the next morning and cleaned it up before Google even realised. However, the same thing happened again over the weekend, and I came into the office to an email from Google: Google has detected that your site has been hacked by a third party who created malicious content on some of your pages. This critical issue utilizes your site’s reputation to show potential visitors unexpected or harmful content on your site or in search results. It also lowers the quality of results for Google Search users. Therefore, we have applied a manual action to your site that will warn users of hacked content when your site appears in search results. To remove this warning, clean up the hacked content, and file a reconsideration request. After we determine that your site no longer has hacked content, we will remove this manual action. _Following are one or more example URLs where we found pages that have been compromised. Review them to gain a better sense of where this hacked content appears. The list is not exhaustive. _ We have again cleaned up the website, however, my problem is that even though we have received this email, I cannot find any evidence of the manual action having actually been applied. I.e. it doesn't show in the Search Console and I am also not getting a warning in the search results when searching for our own website or clicking on the result for our website. That means I cannot submit a reconsideration request - however I am not sure at all there was actually a manual action applied at all based on my test searches. Has anyone here experienced the same issue? What do you suggest doing in this case? Thank you very much in advance for any ideas.
Technical SEO | | ViviCa10 -
Recovery After A Hack - No Manual Action Notice
Hi Guys, I am helping out an agency who have had a couple of site hacked on their server. I can confirm by correlating increase in not found errors and drop in rankings, that the drop was definitely hack based although the site had no manual action notice from Google. The site looks to have been fixed i.e all not found pages look to have been sorted. Obviously there are some dodgy backlinks to now non existant pages but it looks like two months on no sign of a recovery. Is this normal?, Could the site still be hacked and the web designer is claming it has been cleaned up? I am used to dealing with hacked sites when there has been a manual action listed and then it's quite easy to complete the clean up work, submit a reconsideration and then get the manual action revoked but when you don't receieve a manual notification and the site doesn't recover, what do you do? Kind Regards Neil
Technical SEO | | nezona0 -
How To Cleanup the Google Index After a Website Has Been HACKED
We have a client whose website was hacked, and some troll created thousands of viagra pages, which were all indexed by Google. See the screenshot for an example. The site has been cleaned up completely, but I wanted to know if anyone can weigh in on how we can cleanup the Google index. Are there extra steps we should take? So far we have gone into webmaster tools and submitted a new site map. ^802D799E5372F02797BE19290D8987F3E248DCA6656F8D9BF6^pimgpsh_fullsize_distr.png
Technical SEO | | yoursearchteam0 -
Site hacked, but can't find the code
Discovered some really odd words ranking for us in WMT. Looked further and found pages like this www.pdnseek.com/wll/canadian-24-hour-pharmacy. When you click it it redirects to the home page. The developers can't find /wll anywhere on the site. The pages are indexed and cached. Looked at the back links in moz and found many backlinks to our site from other sites using URLs like this. The host says there is nothing on the server, but where else could it be. We've run virus scans, nothing, looked through source code, nothing. Anyone with some idea? www.pdnseek.com is the URL
Technical SEO | | Britewave0 -
Spam pages / content created due to hack. 404 cleanup.
A hosting company's server was hacked and one of our customer's sites was injected with 7,000+ pages of fake, bogus, promotional content. Server was patched and spammy content removed from the server. Reviewing Google Webmaster's Tools we have all the hacked pages showing up as 404's and have a severe drop in impressions, rank and traffic. GWT also has 'Some manual actions apply to specific pages, sections, or links'... What do you recommend for: Cleaning up 404's to spammy pages? (I am not sure redirect to home page is a right thing to do - is it?) Cleaning up links that were created off site to the spam pages Getting rank bank // what would you do in addition to the above?
Technical SEO | | GreenStone0 -
Website hacked
Hi I've been asked to help a colleague with his website. It seems to be hacked. He recently received an e-mail from Google saying his adwords account was suspended 'due to high probability his site may be hosting or distributing malicious software' I just checked his source and there seems to loads of weird on code on his pages, this would not have been but on by any members of the website owners. Please image attached when we try to access his website via google search I just contacted the hosting provider - does anyone have experience with this and how to prevent such hacking in the future. The site is build using HTML with no CMS. IjW19.jpg
Technical SEO | | Socialdude0 -
RSS Hacking Issue
Hi Checked our original rss feed - added it to Google reader and all the links go to the correct pages, but I have also set up the RSS feed in Feedburner. However, when I click on the links in Feedburner (which should go to my own website's pages) , they are all going to spam sites, even though the title of the link and excerpt are correct. This isn't a Wordpress blog rss feed either, and we are on a very secure server. Any ideas whatsoever? There is no info online anywhere and our developers haven't seen this before. Thanks
Technical SEO | | Kerry220